6.001, Spring Semester, 1998---Recitation -- Friday, May 8
MASSACHVSETTS INSTITVTE OF TECHNOLOGY
Department of Electrical Engineering and Computer Science
6.001---Structure and Interpretation of Computer Programs
Spring Semester, 1998
Recitation -- Wednesday, May 6
Summarize the main points of the lecture of May 7. Take a position on what you think the future role of computer assisted surgery will be in medicine, and whether you think computers should be used to aid surgeons in delicate surgery such as neurosurgery.
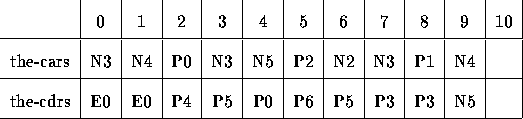
Memory consists of many cells. Each cell stores the following: A
number and a tag. For now, we have three tags:
``N'' -- Number
``P'' -- Pointer to another cell
``E'' -- NULL

Using this implementation of cons cells, (cons A B) does this:
 , a pointer to the new cons cell.
, a pointer to the new cons cell.
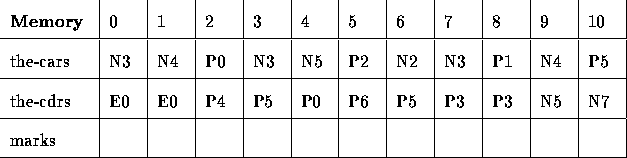
Using the memory block above, draw the box-and-pointer diagram starting from P5.
Note that not everything sitting in memory is useful. For example, consider what occurs when the following is evaluated (define foo (map square (list 1 2 3))).
There are no pointers to the list (1 2 3) anymore. It cannot be accessed. It is garbage. The memory should be recycled.
Does our computer have infinite memory? No. But we can create the illusion of infinite memory using Garbage Collection. Consider the following four procedure. When applied, will Scheme run out of memory or go into an infinite loop?

What's Garbage? Garbage is anything that cannot have any influence on the future computation. Everything else we need to keep around. We define the Root Set to be the set of all pointers in the machine registers and stack. The cells we might need are defined as those cells that can be reached by a succesion of car and cdr operations starting from the root set.
Here's the main idea to reference counting:
Consider the following example, and draw the box-and-pointer diagrams below, keeping a ``reference counter'' with each cell.
(define a (list 1 2 3)) (set-cdr! a 4) (set-cdr! a a) (set! a 1)
Reference Counting can't handle circular data structures!
Here's the main idea to Stop and Copy:
The register machine code for this algorithm is in the text.
For example, let's perform stop-and-copy on the following with Root Set = { P5 }:
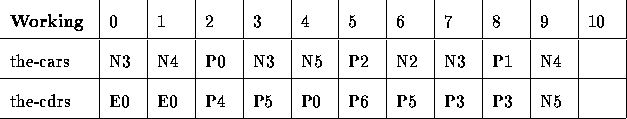
This method sounds expensive, because half of memory is idle except when using the Garbage Collector. However, it goes just about as fast as possible. It only examines valid locations. Most memory is garbage, and never even gets looked at. We see a very common tradeoff here: Pay a lot of space, get a lot of time.
Here's the main idea to Mark-Sweep:
For example, let's perform Mark-Sweep on the following with Root Set = { P5 }:
Stack:
Free Pointer:
This method is a good deal more compact than stop-and-copy. However, it also always looks through all of memory, so it is fairly slow.
In this example, we needed a stack to keep track of where we still need to explore. This can actually be done without a stack by keeping track of recursive calls using the data structures in memory themselves.